Setup SSL certificate for MiaRec Web portal on Centos
In order to enable HTTPS (SSL) in MiaRec Web server, it is necessary to install SSL certificate. The certificate should be issued from a trusted Certificate Authority (like Verisign/Symantec, Comodo, GlobalSign, Digicert, GoDaddy etc).
The certificate is issued per domain name and can be used only with particular name. For example, if you install MiaRec on server and access it with address https://rec.my-company.com, then the SSL certificate should be issued to “rec.my-company.com” domain name.
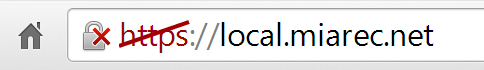
Alternatively, the certificate can be self-signed. This means that instead of signing the certificate by Trusted Authority, you will sign it by your own certificate. In this case you will see in browser warning message that certificate is not trusted (means that it is not signed by trusted Certificate Authority), although the connection between client’s web-browser and MiaRec server will be secure and encrypted:
You can generate the self-signed certificate using the following command line:
openssl req -new -newkey rsa:2048 -days 3650 -nodes -x509 -keyout server.key -out server.crt
This command will generate key/certificate pair and then sign it.
1. Install mod_ssl module for Apache
yum install mod_ssl
The module will automatically be enabled during installation, and Apache will be able to start using an SSL certificate after it is restarted. You don't need to take any additional steps for mod_ssl to be ready for use.
2. Install SSL private key and certificate
Copy your SSL private key to directory:
/etc/pki/tls/private/
Copy your SSL certificate to directory:
/etc/pki/tls/certs/
In some case you may need to copy also intermediary certificate of the company, which signed your certificate. Check their official instructions for Apache server.
3. Edit Apache configuration file (ssl.conf)
Edit file /etc/httpd/conf.d/ssl.conf and make sure that:
SSLCertificateFilepoints to your certificateSSLCertificateKeyFilepoints to your private certificateSSLCertificateChainFilepoints to your certificate authority intermediary certificate (check your authority instructions)
# Server Certificate:
SSLCertificateFile /etc/pki/tls/certs/miarec.example.com.crt
# Server Private Key:
SSLCertificateKeyFile /etc/pki/tls/private/miarec.example.com.key
# Server Certificate Chain:
SSLCertificateChainFile /etc/pki/tls/certs/CA.crt
4. Disable SSL protocol, allow TLS v1.2 only
It is recommended to disable SSL version 3.0 protocol, and force clients to use more secure TLS v1.2
Edit file /etc/httpd/conf.d/ssl.conf, locate the SSLProtocol line, if its commented out with a #, remove the hash (#) symbol and change it to the following:
SSLProtocol TLSv1.2
Now to increase the security strength we can also disable the weaker ciphers, located the SSLCipherSuite line, uncomment it and make it:
SSLCipherSuite HIGH:MEDIUM:!SSLv3:!kRSA:!RC4:!3DES
5 Disable TRACE method
Add the following line to the end of file /etc/httpd/conf/httpd.conf:
TraceEnable off
6. Open port 443 on firewall
Add exclusion rule to firewall:
iptables -I INPUT 5 -i eth0 -p tcp --dport 443 -m state --state NEW,ESTABLISHED -j ACCEPT
Save all rules into iptables configuration file:
service iptables save
Restart iptables service:
service iptables restart
7. [Optional] Force HTTPS for all traffic except internal call events
Create file /etc/httpd/conf.d/miarec-ssl.conf:
vi /etc/httpd/conf.d/miarec-ssl.conf
Copy/paste the following content into this file:
NameVirtualHost *:80
<VirtualHost *:80>
RewriteEngine on
RewriteCond %{HTTP_HOST}%{REQUEST_URI} !^127.0.0.1/notify
RewriteRule ^/(.*) https://%{HTTP_HOST}/$1 [NC,R=301,L]
</VirtualHost>
Reload Apache:
service httpd reload
What is "127.0.0.1/notify" in the rewrite rule? MiaRec uses internally the HTTP protocol for sending call event notifications from recorder engine to a web portal. The above rewrite rule will force HTTPS for all web traffic except internal communication between recorder and web portal.
8. Restart Apache
service httpd restart