Optional Configuration
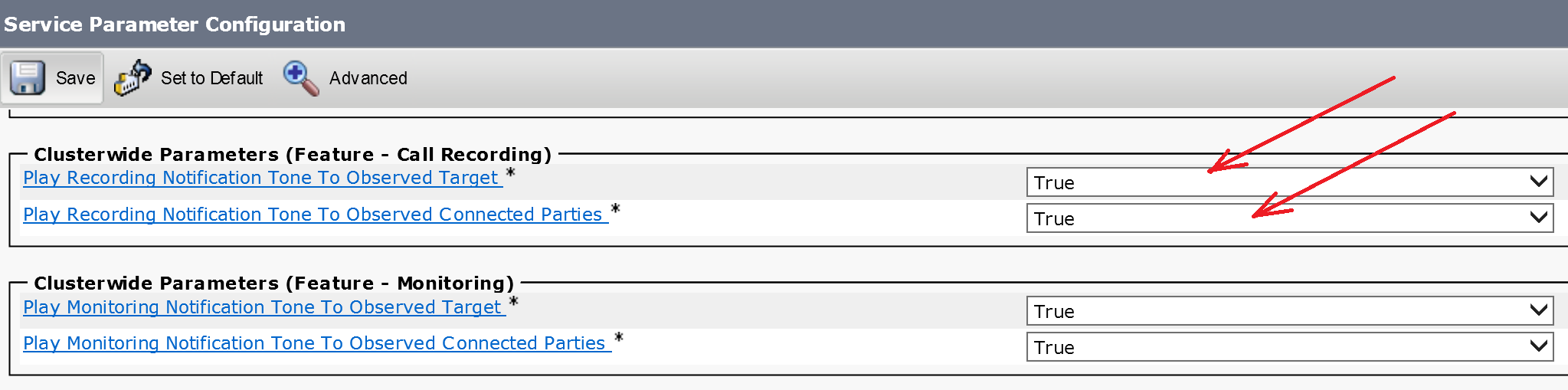
Configure notification tones for recording
The recording notification tones can be played either to the agent only, the customer only, or to both.
Use the System > Service Parameters menu option in Cisco Unified Communications Manager Administration and navigate to the Clusterwide Parameters (Feature – Call Recording) group to peform the nessessary configuration:
[How To] Configure SIP/TLS for SIP Trunk
This page describes how to configure a SIP/TLS encrypted connection for SIP Trunk towards MiaRec recorder in Cisco UCM.
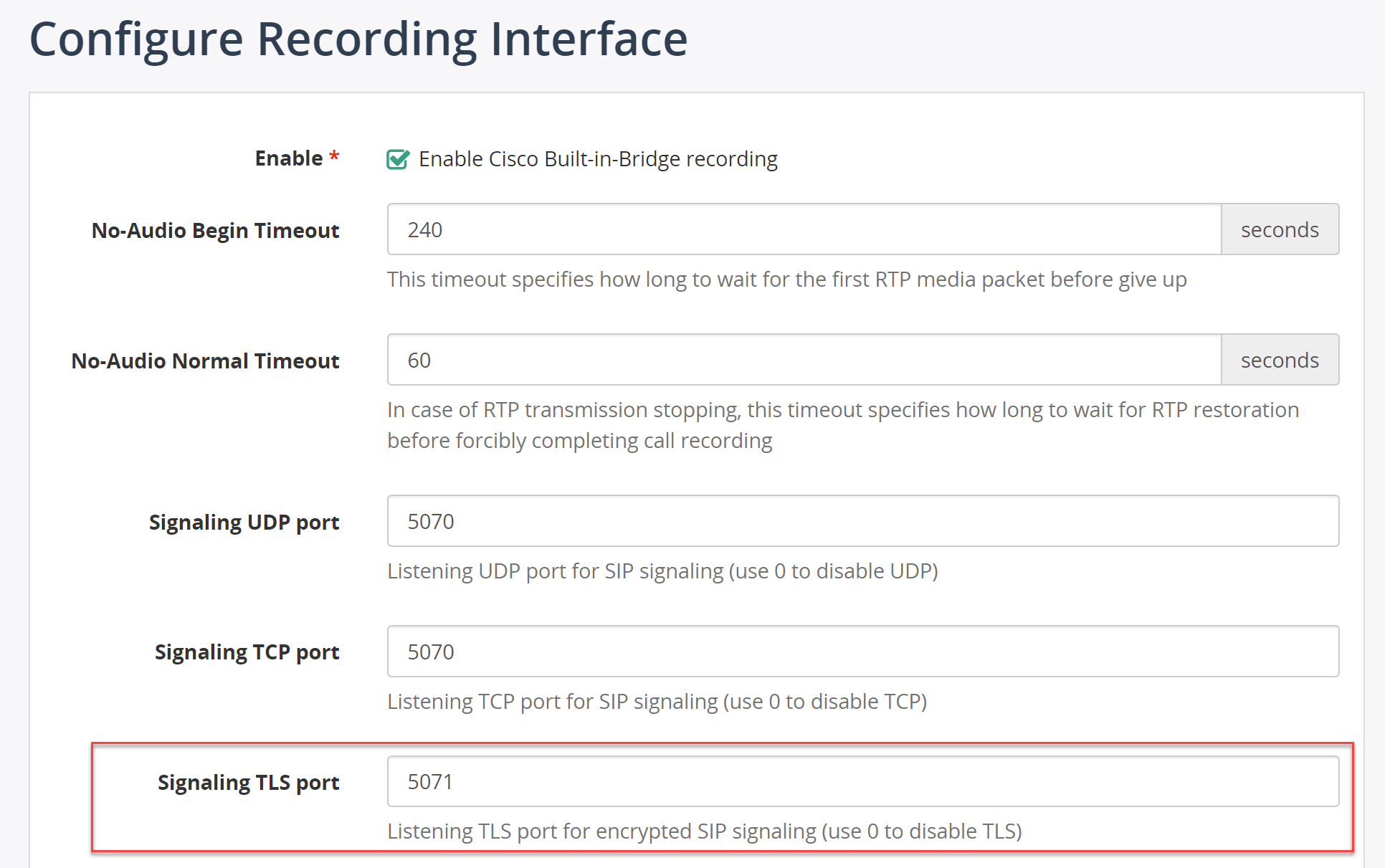
Configure Signaling TLS port in MiaRec
Navigate in MiaRec web portal to Administration -> Recording Interfaces -> Cisco BiB Configuration.
Configure the listening port in parameter Signaling TLS port, for example port 5071.
Info
If the firewall is enabled on the MiaRec server, make sure it allows an inbound connection to this port.
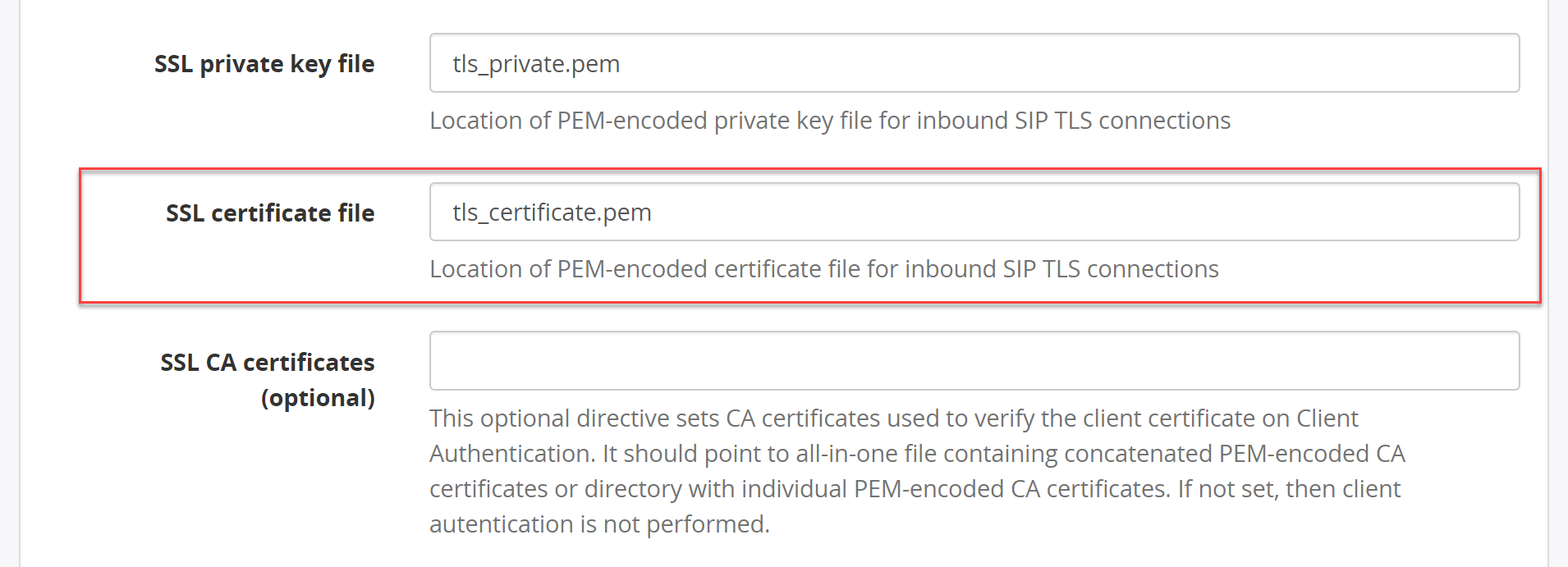
MiaRec application automatically generates the certificate. The location of the certificate file is configured in the same screen in the SSL certificate file parameter. By default, the value is tls_certificate.pem.
Locate this file on the MiaRec recording server. We will need to import this file into CUCM.
On Windows, the file is located in the same directory as MiaRec.exe file (by default, C:\Program Files (x86)\MiaRec Business\Bin).
On Linux, the file is located at /opt/miarec/shared or in older versions at /var/lib/miarec.
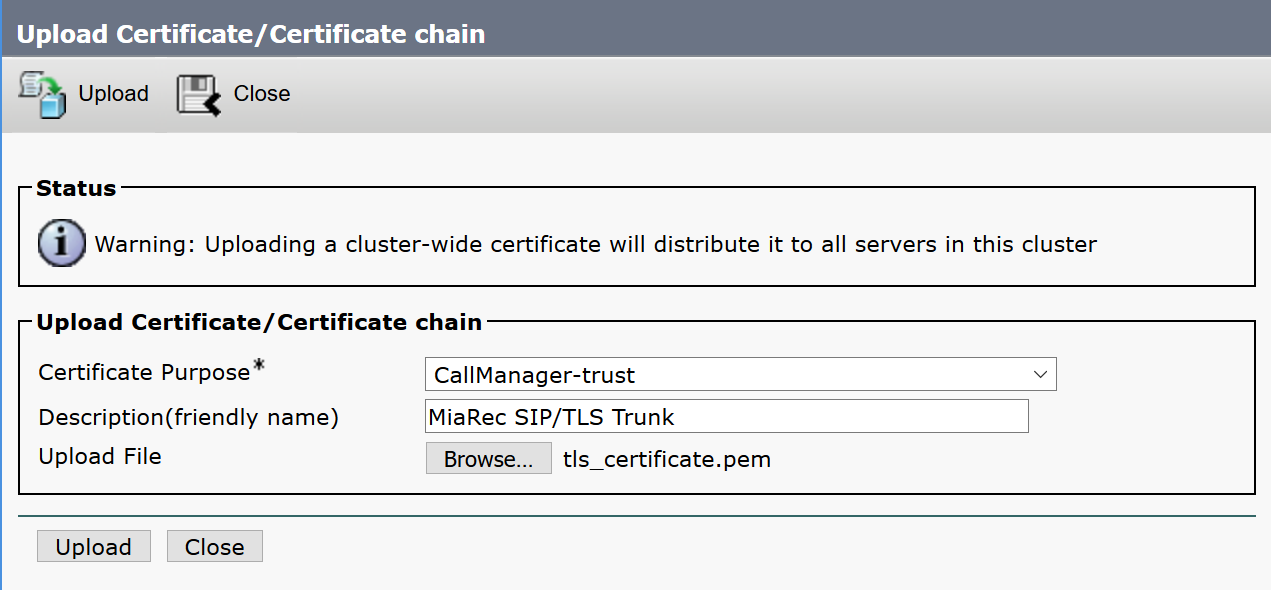
Import MiaRec SSL certificate into Cisco UCM
Login to Cisco Unfied OS Administration using Cisco UCM admin password. Navigate to Security > Certificate Management and click Upload Certificate/Certificate Chain.
- In the Certificate Purpose field, select CallManager-trust
- Use the Browse button to upload the SSL certificate file from the MiaRec server
Configure SIP Trunk Security Profile
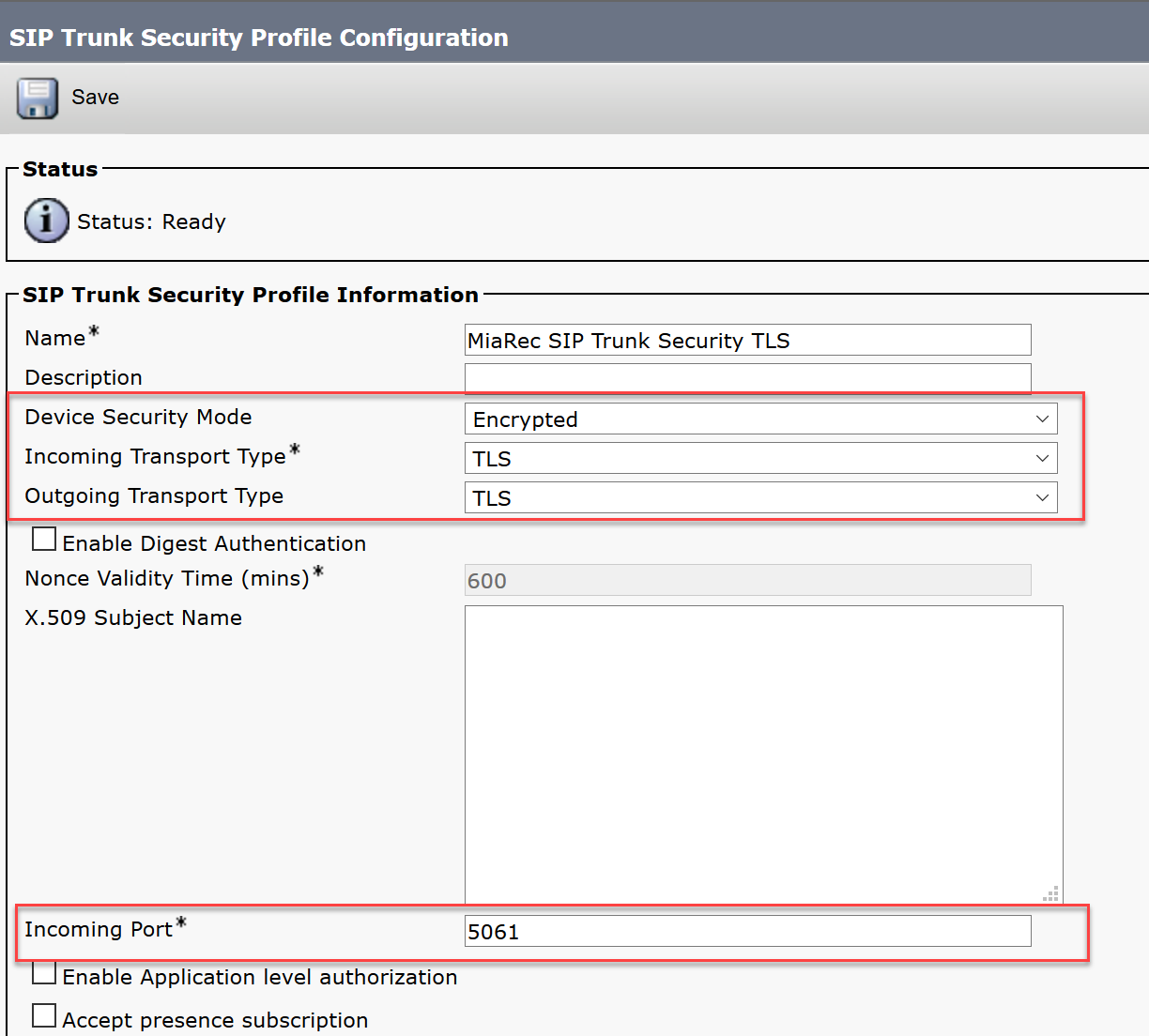
Use the System > Security > SIP Trunk Security Profile menu option in Cisco Unified Communications Manager Administration to create SIP Trunk Security profile for SIP/TLS connection to the MiaRec recording server.
- In the Device Security Mode field, select Encrypted.
- In the Incoming Transport Type field, select TLS.
- In the Outgoing Transport Type field, select TLS (this setting has to match the configuration of MiaRec).
- Uncheck the Enable Digest Authentication option.
- In the Incoming Port field, specify a unique port. CUCM will send SIP messages to MiaRec from this port. CUCM requires a unique port for each configured SIP Trunk. If the default port 5061 is busy, then try another port like 5062, 5063, etc.
Configure SIP Trunk
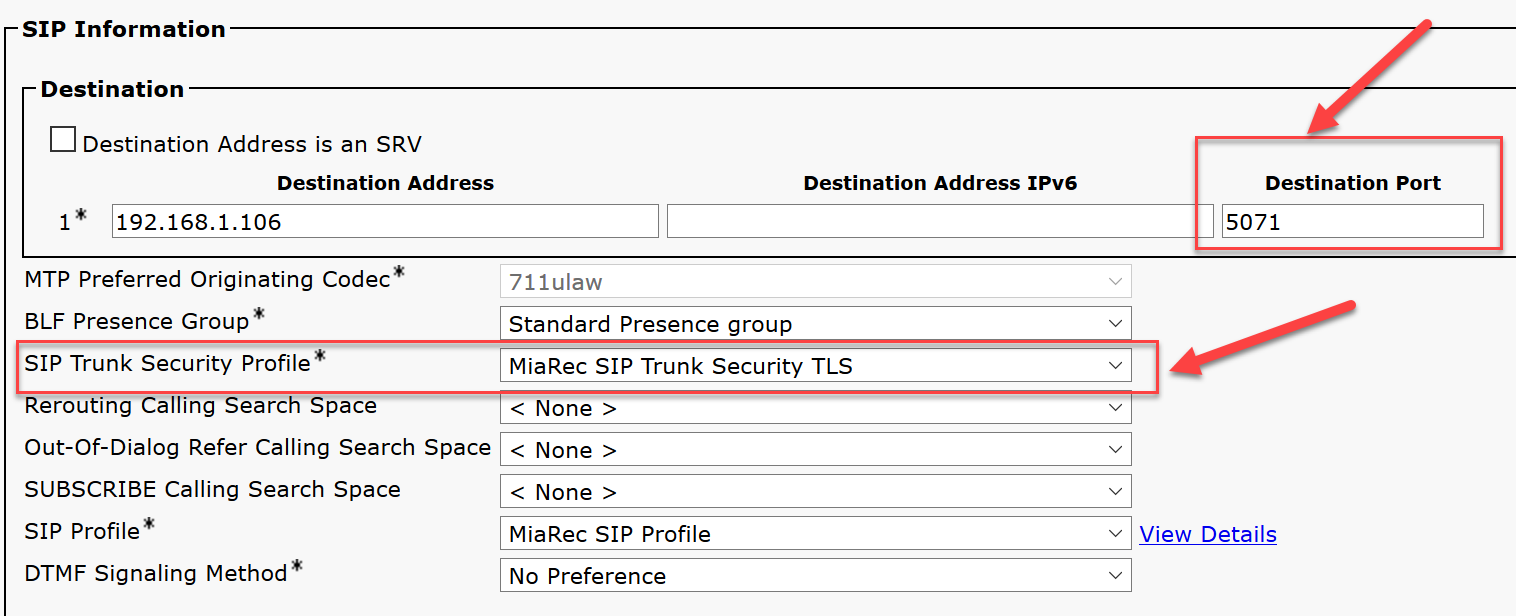
Use the Device > Trunk menu option in Cisco Unified Communications Manager Administration to edit the previously created non-secure SIP trunk that points to the MiaRec recorder.
In the SIP Information section, provide the following configuration:
- Destination Port should match the port on which the MiaRec recorder is listening for the messages from CUCM (5071 in our example).
- Select the previously created SIP Trunk Security Profile (TLS) for the recorderz.
Click the Reset button for this trunk to reload CUCM configuration.
Troubleshooting
Enable trace logging in MiaRec (menu Administration > Maintenance > Troubleshooting) and look for any error messages related to TLS.
A successful establishment of the TLS connection produces the following output in the trace.log file:
2018/01/03 09:46:59.028 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(195) Constructed context: method=SSLv23 ctx=09153A88
2018/01/03 09:46:59.028 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(510) Constructed channel: ssl=09164AF8 method=SSLv23 context=00747C48
2018/01/03 09:46:59.028 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) General: state=before/accept initialization
2018/01/03 09:46:59.028 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=before/accept initialization
2018/01/03 09:46:59.082 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 read client hello A
2018/01/03 09:46:59.082 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 write server hello A
2018/01/03 09:46:59.082 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 write certificate A
2018/01/03 09:46:59.088 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 write key exchange A
2018/01/03 09:46:59.088 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 write server done A
2018/01/03 09:46:59.088 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 flush data
2018/01/03 09:46:59.136 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 read client key exchange A
2018/01/03 09:46:59.136 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 read finished A
2018/01/03 09:46:59.136 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 write session ticket A
2018/01/03 09:46:59.136 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 write change cipher spec A
2018/01/03 09:46:59.136 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 write finished A
2018/01/03 09:46:59.136 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSLv3 flush data
2018/01/03 09:46:59.136 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) General: state=SSL negotiation finished successfully
2018/01/03 09:46:59.136 09:46:58.835 4 OpalListener:4b64 PSSLChannel.cxx(22) Accept: state=SSL negotiation finished successfully
2018/01/03 09:46:59.136 09:46:58.835 1 OpalListener:4b64 TransportTLS.cxx(144) TLS Started connection to 192.168.1.200:34226 (if=192.168.1.106:5071)
2018/01/03 09:46:59.136 09:46:58.835 4 OpalListener:4b64 ListenerTLS.cxx(49) TLS Listen Waiting on socket accept on tls$*:5071
2018/01/03 09:46:59.137 09:46:58.835 3 TransportHandler:467c Listener.cxx(93) Listen Started handler thread on tls$192.168.1.200:34226<if-read=tls$192.168.1.106:5071, if-write=tls$192.168.1.106:5071> 0x09160FC0
2018/01/03 09:46:59.137 09:46:58.835 3 TransportHandler:467c CiscoBiBManager.cpp(185) CiscoBiB Listener thread started on tls$192.168.1.200:34226<if-read=tls$192.168.1.106:5071, if-write=tls$192.168.1.106:5071> 0x09160FC0
2018/01/03 09:46:59.137 09:46:58.835 3 TransportHandler:467c SipPdu.cpp(156) SIP PDU Created: <<Uninitialised>> CSeq=
2018/01/03 09:46:59.161 09:46:58.835 5 TransportHandler:467c SipPdu.cpp(671) SIP PDU Parsed 399 bytes on tls$192.168.1.200:34226<if-read=tls$192.168.1.106:5071, if-write=tls$192.168.1.106:5071> 0x09160FC0
2018/01/03 09:46:59.161 09:46:58.835 4 TransportHandler:467c SipPdu.cpp(734) SIP PDU Received 399 bytes on tls$192.168.1.200:34226<if-read=tls$192.168.1.106:5071, if-write=tls$192.168.1.106:5071> 0x09160FC0
OPTIONS sip:192.168.1.106:5071 SIP/2.0
Content-Length: 0
Contact: <sip:192.168.1.200:5061;transport=tls>
User-Agent: Cisco-CUCM11.5
Call-ID: 17095a80-a4d11712-19475-c801a8c0@192.168.1.200
CSeq: 101 OPTIONS
Date: Wed, 03 Jan 2018 17:46:58 GMT
Via: SIP/2.0/TLS 192.168.1.200:5061;branch=z9hG4bK1959e66d3ef22
From: <sip:192.168.1.200>;tag=275457321
Max-Forwards: 0
To: <sip:192.168.1.106>
Contact a MiaRec representative if you face any issues.\